iSOC
Intelligence Driven SOC (iSOC) for Government and Critical Service Providers
Syborg iSOC combines leading big data analytics and machine learning technologies, deep domain expertise and intelligence methodologies to drive intelligence into security operations.
SECURE YOUR FUTURE WITH A GOVERNMENT-GRADE SOC
Whether building a SOC from the ground up or advancing your existing security operations, Syborg’s iSOC platform offers governments and critical infrastructure providers a combination of technology, domain expertise, intelligence methodology and professional services - streamlining SOC operations, ensuring regulatory compliance and reducing the total cost of ownership
Accelerate Threat
Detection and Response
Detection and Response
Detect complex threats early on, automatically investigate 100% of alerts and rapidly respond to security incidents
Empower Your
SOC Team
SOC Team
Reduce the number of security tools to accelerate onboarding, lower skills barriers and focus the SOC analysts on business-critical issues.
A Single
Platform Solution
Platform Solution
End-to-end iSOC setup, including Syborg’s detection and response, SIEM, Threat Intelligence Platform & third-party integrations, SOC methodologies, training and personnel.
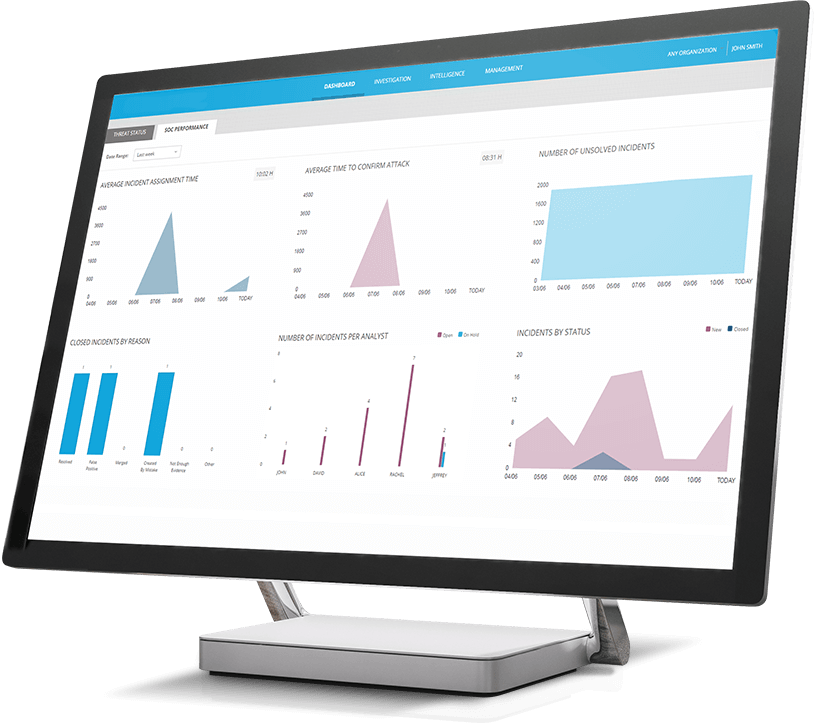
Accelerate the path from Detection to Response with Automated Cyber Investigations
- Early detection of unknown threats via multiple detection sensors, leveraging machine learning, big data and behavioral analysis.
- Automatically investigate 100% of alerts to remove false positive and uncover high risk security incidents.
- Monitor the open, deep and dark web to reveal cyber threats using Syborg’s Web Intelligence platform
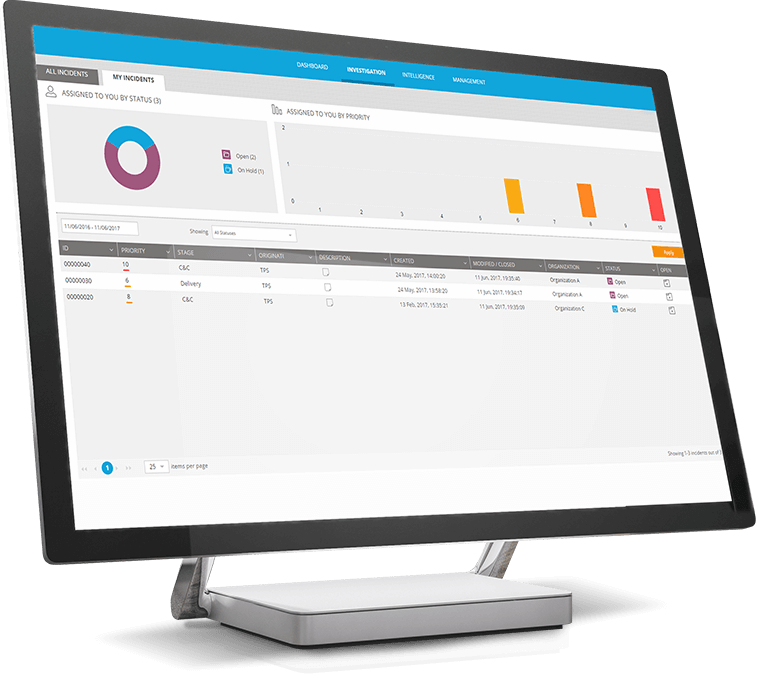
Augment the reality in the SOC to empower your analysts
- Automatically triage, consolidate and prioritize alerts, freeing analysts to focus on business critical tasks.
- Reduce the number of security tools required, with single pane of glass for detection, investigation, forensic gathering & response.
- Accelerate analysts onboarding and lower the skills barrier with simplified cyber investigations, attack storylines and out-of-the-box compliance reports.
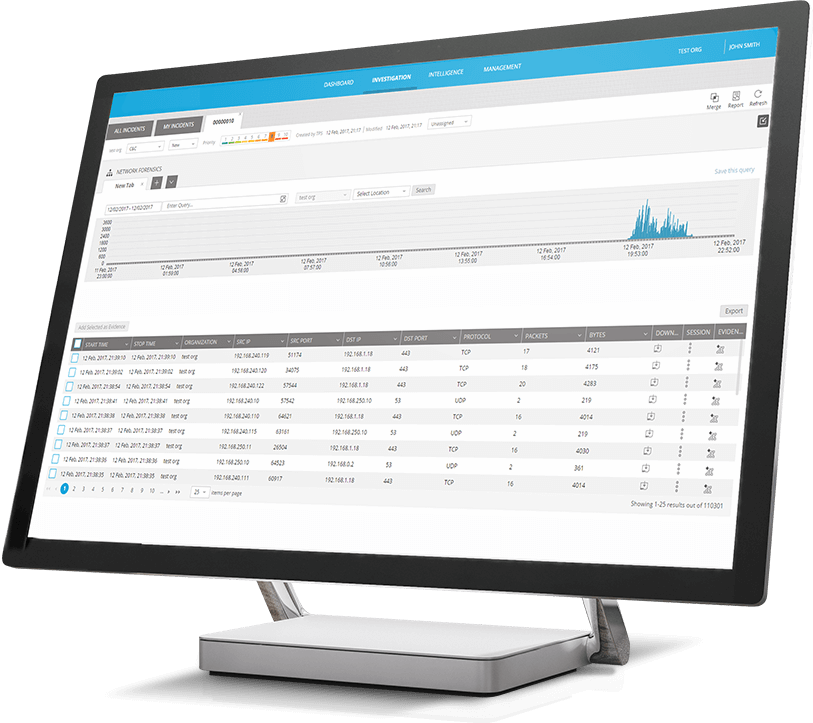
Ground-up SOC setup: Technology, Methodology, Training
- End-to-end iSOC setup including Syborg’s detection and response, SIEM, Threat Intelligence Platform & third-party integrations, SOC methodologies, training and personnel
- SOC Methodologies by Cyber Experts:
incident response, case management, collaboration and reporting - Comprehensive Product, Security and iSOC Methodologies Training, including simulations and professional staffing
